Recent years have seen an unprecedented growth in remote working, with more than half of the world’s workforce now working outside the office at least once per week. Some innovative startups are even eschewing the traditional office environment entirely, instead using cloud technology to connect workforces over a much wider geographical area.
How to get your business ready for remote working
5 Tips for managing your mobile workforce more effectively
What are the advantages of using Citrix Hypervisor to host your virtual machines?

Virtualization greatly enhances computing efficiency by consolidating resources into a flexible, software-defined architecture. One of the core components of such an infrastructure is the hypervisor, a specialized software application that separates your desktop operating systems from the underlying hardware.
What is layered network security, and why does it matter?
In a medieval castle, the first line of defense was typically a moat. And if attackers managed to get past the moat, they’d still have high walls to contend with. Inside the castle was a keep, a fortification barricaded behind stone walls and iron portcullises that was the most secure part of the estate.
Understanding the lingo: A glossary of common business IT terms

Confused by the barrage of IT acronyms and technical jargon? Let’s speak in plain language to better understand the role of modern technology in business IT. Here are some of the most common terms you’ll come across when evaluating technology solutions and vendors:
Asset management
In the technology sector, asset management refers to the methodology for managing every IT system used in the business.
A cybersecurity and compliance checklist for healthcare organizations
5 Misconceptions about cloud computing that need to go
5 Tips to prevent data breaches in your healthcare organization
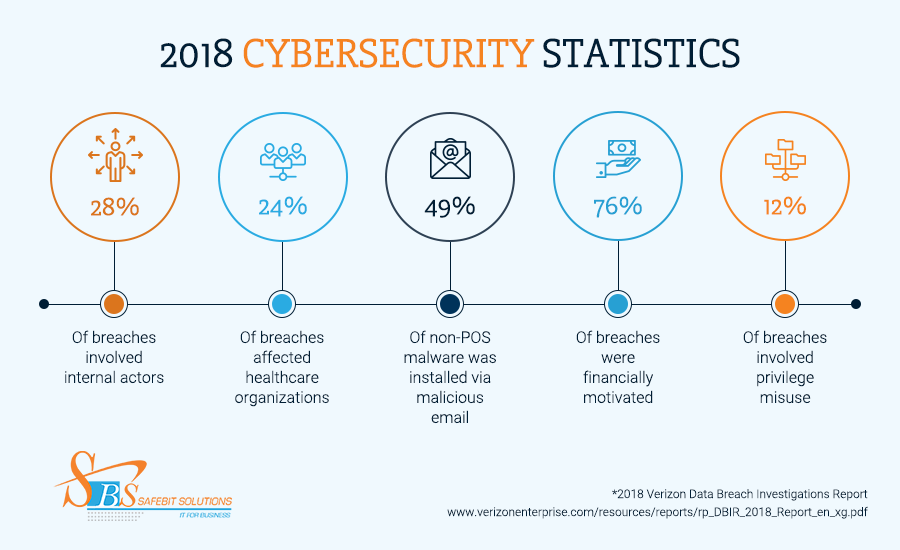
Healthcare organizations and their business associates operate within one of the most tightly regulated industries of all. Given the nature of the data they hold, this shouldn’t come as any surprise.
What many healthcare leaders aren’t aware of, however, is that despite these strict requirements, they’re still favorite targets for hackers, ransomware purveyors, and other malefactors.







